In today’s digital landscape, even well-respected companies can fall victim to sophisticated cyber-attacks. One such incident allegedly involved Warby Parker, the popular eyewear retailer, which was fined $1.5 million for a HIPAA violation following a credential stuffing attack. This breach not only compromised the personal information of approximately 200,000 customers but also highlighted some significant oversights in cybersecurity practices that can have far-reaching consequences.
In this blog, we will explore what happened, how credential stuffing works, the key HIPAA compliance failures, and how your organization can learn from these mistakes. We will also discuss practical steps to safeguard your systems—including how Securden’s password manager can play an essential role in strengthening your defences.
Understanding the Warby Parker Incident
In 2018, Warby Parker allegedly suffered a data breach due to a credential stuffing attack, where hackers used stolen credentials from other breaches to access accounts. Since many users reuse passwords, nearly 200,000 customers' personally identifiable information (PII) was reportedly compromised.
The breach's impact worsened as Warby Parker purportedly failed to secure sensitive electronic Protected Health Information (ePHI), violating HIPAA regulations. This led to a significant fine and reinforced the need for strict security measures when handling sensitive data.
Warby Parker’s Alleged HIPAA Violations
HIPAA requires strict safeguards for ePHI, and Warby Parker reportedly fell short in three key areas:
- Lack of Risk Identification – They failed to fully assess and document potential threats to ePHI, making it harder to mitigate vulnerabilities.
- Weak Risk Reduction Measures – Security controls were allegedly insufficient to prevent unauthorized access, leaving them exposed to credential stuffing attacks.
- Failure to Monitor System Activity – Inadequate log reviews meant suspicious activity went undetected, increasing breach risks.
These lapses highlight the need for continuous risk assessment, strong security measures, and proactive monitoring to maintain HIPAA compliance.
What is Credential Stuffing?
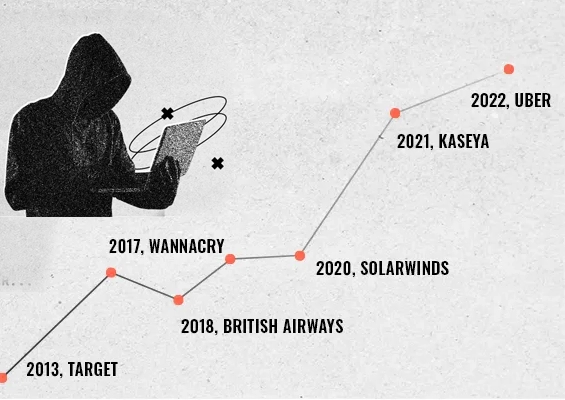
Credential stuffing is a widespread, dangerous cyberattack that exploits reused passwords across multiple sites. Attackers obtain compromised credentials from one breach, then automate login attempts elsewhere, hoping for matches. Successful logins grant unauthorized account access, often leading to further breaches and privacy violations. Because these attacks are automated, they’re especially tough to stop without proper tools and strategies. The Warby Parker incident is a stark reminder that even reputable companies are not immune.
Lessons Learned from the Warby Parker Case
The Warby Parker incident provides the following important takeaways for organizations, particularly for those handling sensitive customer data or operating under regulatory frameworks such as HIPAA:
- Comprehensive Risk Assessments Are Essential: Organizations must regularly evaluate their systems for vulnerabilities and document all potential risks. A thorough risk assessment not only helps in identifying areas that need improvement but also serves as a critical tool for regulatory compliance.
- Implement Robust Security Measures: Merely having security measures in place is not enough. These measures need to be robust and up-to-date to combat evolving cyber threats. Warby Parker’s failure to enforce sufficient risk reduction measures left them exposed to credential stuffing attacks.
- Regular Monitoring and Incident Response: Establishing processes to regularly review system activity can help detect unauthorized access early. An effective incident response plan ensures that, in the event of a breach, the organization can act quickly to mitigate damage.
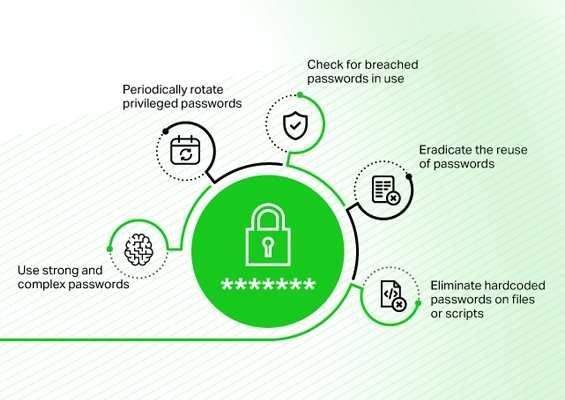
- The Importance of Cyber Hygiene: Simple practices like enforcing strong password policies, using multi-factor authentication, and blacklisting commonly breached passwords can go a long way in defending against credential stuffing.
Ways to Prevent Your Organization from Credential Stuffing
Given that credential stuffing is a widespread and persistent threat, organizations must adopt a multi-layered approach to security. Here are some key measures that can help protect against these attacks:
- Enforce a Strong Password Policy
Encourage employees and users to create complex, unique passwords. A strong password policy minimizes the risk of successful brute-force or credential stuffing attempts. - Blacklist Common or Previously Breached Passwords
Prevent the use of passwords that are commonly used or have been compromised in past breaches. This step can significantly reduce the risk of credential reuse across platforms. - Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to verify their identity through multiple means, making it much harder for attackers to gain access even if they have the correct password. - Conduct Regular Security Audits
Periodically review your systems for vulnerabilities. Regular audits help ensure that security measures are up-to-date and effective in combating current threats. - Set Up Credential Monitoring
Use tools like “Have I Been Pwned” to monitor if your usernames and passwords have been compromised in other breaches. Early detection is key to preventing further exploitation. - Apply Rate Limiting or Throttling
Implement rate limiting at the API level to prevent automated login attempts from overwhelming your systems. This makes it harder for attackers to carry out large-scale credential stuffing. - Deploy Anomaly Detection Tools
Leverage advanced tools to identify suspicious login behaviour and other anomalies. Early detection systems can alert you to potential breaches before they escalate.
Best Practices for HIPAA Compliance
For organizations that fall under HIPAA regulations, there are additional steps to ensure that ePHI is protected and they are,
- Identify ePHI Data Locations
Leverage advanced tools to identify suspicious login behaviour and other anomalies. Early detection systems can alert you to potential breaches before they escalate. - Integrate Risk Analysis into Business Processes
Embed risk analysis and management into your everyday business operations. This proactive approach helps in identifying potential vulnerabilities before they can be exploited. - Ensure Proper Audit Controls
Implement robust audit controls that record and examine system activity. Regular audits can help in identifying unauthorized access and other anomalies. - Conduct Regular Reviews
Maintain ongoing reviews of system logs and activity records. Regular reviews help detect and address issues promptly. - Utilize Strong Authentication Mechanisms
Ensure that only authorized users can access ePHI by implementing strong authentication measures, including MFA. - Encrypt ePHI in Transit and at Rest
Use encryption to safeguard sensitive data both during transmission and while it is stored. Encryption acts as a final line of defense against unauthorized access. - Learn from Incidents
Analyze security breaches when they occur and integrate the lessons learned into your overall security strategy. Continuous improvement is key to staying ahead of cyber threats. - Provide Regular Training Conduct ongoing HIPAA-specific training sessions for your workforce. Regular training helps ensure that all employees understand the importance of compliance and the best practices for maintaining it.
How Securden’s Password Vault Can Help
In the battle against credential stuffing and other cyber threats, having the right tools can make a significant difference. Securden’s password manager- Password Vault is designed to bolster your organization’s security posture by providing robust password management solutions. Here’s how it can help:
- Strong Passwords, No Reuse – Generates complex, unique passwords to prevent reuse, a key weakness in credential stuffing.
- Secure Storage & Encryption – Safeguards credentials with advanced encryption, keeping passwords protected even if a system is compromised.
- Multi-Factor Authentication – Adds an extra security layer, preventing unauthorized access even if passwords are leaked.
- Dark Web Monitoring – Detects exposed credentials and alerts users, enabling quick action to prevent breaches.
- User-Friendly Experience – Simple, intuitive design ensures easy adoption, making strong security effortless for all employees.
Integrating Securden’s password manager minimizes the risk of credential stuffing by enforcing strong password policies and ensuring HIPAA compliance.
The Warby Parker breach highlights that no organization is immune to cyber threats. Credential stuffing can lead to financial and reputational damage, making robust security measures—such as MFA, regular audits, and proactive monitoring—essential, especially for healthcare organizations.
Securden’s Password Vault for Enterprises streamlines password management, enforces strong security protocols, and helps maintain compliance. In today’s digital world, cybersecurity isn’t optional—it’s critical for protecting sensitive data and maintaining customer trust.







![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)